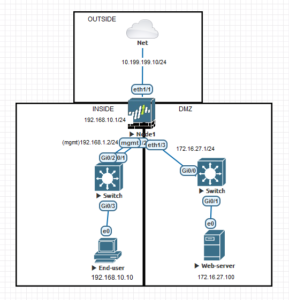
Palo Alto firewall policies configuration example with 3 Zones – Internal, DMZ, and Outside
In the following steps I show the policies that need to be configured in order to reach the following requirements: In the internal network, there is an end-user client, in the DMZ a web server, and both networks are configured to access the internet only with web-browser (it is not possible to access the port 80/443 with anything else but a web-browser (for example telnet to the 443 port is not allowed). It is possible to access the webserver from the outside, but it’s not possible to access the internal network from the outside zone. It is possible from the internal network to access the DMZ network, but the DMZ is not allowed to access the internal network.
Internet access based in application (web browser)
Inside -> DMZ web access, ssh access
Outside > DMZ web access
INITIAL CONFIGURATION
- Login to the device with the default username and password (admin/admin).
- Enter configuration mode using the command configure
- Change the system setting to static (DHCP is enabled by default) admin@fw# set deviceconfig system type static
- Use the following command to set the IP address of the management interface: admin@fw# set deviceconfig system ip-address 192.168.1.1 netmask 255.255.255.0 default-gateway 192.168.1.1 dns-setting servers primary 8.8.8.8
- Commit the changes using the command commit
- Exit configuration mode by using the command exit and then confirm the configurations by running the command show interface management.
INTERFACES CONFIGURATION:
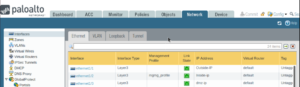
Interface1/1 – Outside zone
Interface 1/2 – Inside zone
Interface 1/3 – DMZ zone
Notice the mgmg_profile configure in the interface 1/2, this allows the management access through that interface.
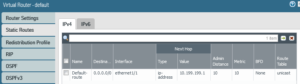
DEFAULT ROUTE TO THE INTERNET
In the virtual router configuration I add the three interfaces in used (outside, inside, dmz)
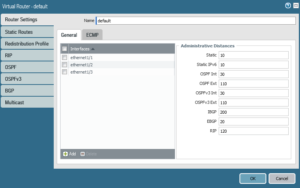
And I set the default route to go out through the interface ethernet 1/1 with the next-hop of 10.199.199.1
SECURITY POLICY – ACCESS TO THE INTERNET USING ONLY THE WEB BROWSER APPLICATION FROM INSIDE AND DMZ ZONES
The Rule type should be set to interzone

The sources are any ip addresses coming from the dmz or inside zones

The destination is any ip address through the outside zone

The only application allowed is web browsing

The rule is set to allow

NAT POLICY TO ALLOW INTERNET FROM THE INSIDE AND DMZ ZONES
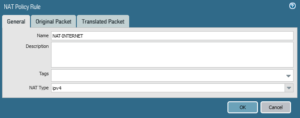
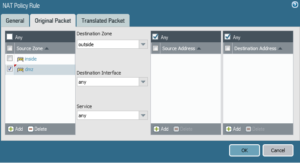

Now notice how it is possible to access any type of content in the internet through the web browser from the internal or DMZ zones
But any other type of internet access is blocked by the security policy previously created
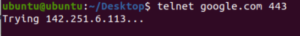
One of the best features of Palo Alto Networks is the ability to filter/block traffic based on applications and not just by network ports. For example, as we could see the web browsing is perfectly allowed while accessing the web page using mozilla firefox with https traffic through port 443. If we generate traffic with any other type of application for example with Telnet using the port 443 that traffic would be blocked.
So Palo Alto is able to differentiate between which type of application you are using to access certain resources and it counts with a huge library of applications that allows to really make sure the most important type of accesses in the organization are covered. A lot of hackers try to tunnel or mask traffic for example ssh traffic through the DNS port or HTTP/HTTPs ports as a backdoor entrance into an internal server.
If I enable any application in the security policy and like a traditional firewall allow the ports 80/443 for http/https access, dns 53 port is needed as well.
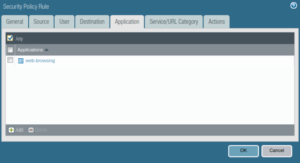
We are going to be able to access any web server on the internet as well
But now I can access the https/http server using telnet which is obviously not the intended type of access for a webserver.
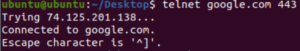

So Palo Alto is able to differentiate between which type of application you are using to access certain resources and it counts with a huge library of applications that allows to really make sure the most important type of accesses in the organization are covered. A lot of hackers try to tunnel or mask traffic for example ssh traffic through the DNS port or HTTP/HTTPs ports as a backdoor entrance into an internal server. This gives the hackers creativity to exploit the applications in non-unauthorized ways.
ACCESS FROM OUTSIDE TO DMZ
First I create a security policy to allow only web-browser access from the outside zone (internet) to the DMZ using the application based rule instead of the specific ports. Notice that the destination IP address should be the public IP of the web-server.
Now I create a NAT policy to translate the external ip 10.199.199.100 with the internal ip 172.16.27.100 (web-server)

Note the destination zone, in this case, should be outside
Now it is possible to access the nginx webserver located in the dmz zone
WEB AND SSH ACCESS FROM THE INSIDE TO THE DMZ ZONE
The following are the steps as explained before to add a new security rule that would allow web-browing and ssh applications from the inside zone to the DMZ zone

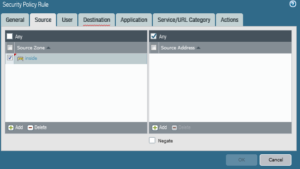

Never forget that you need to commit the configuration in order for the changes to take effect
Now, it is possible to access the ssh and http services in the DMZ from the inside Zone